CYS4 & SecureFlag: A new Advanced Practical SOC Training Platform
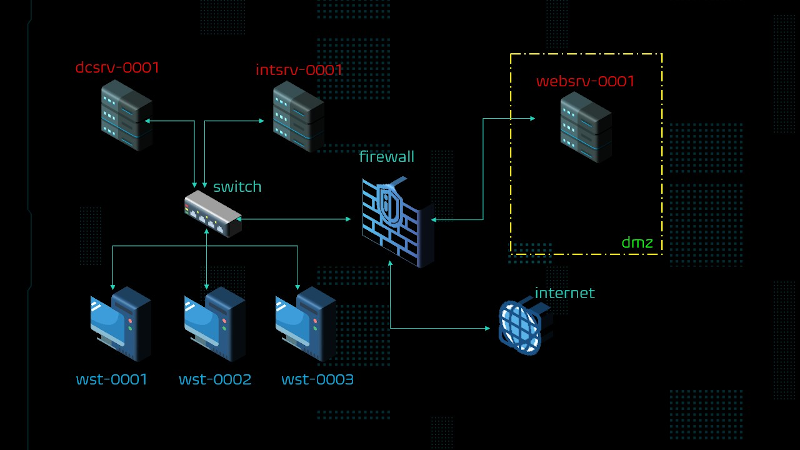
Table of contents
- Introduction
- Why is it made?
- How we solve this problem?
- Who is it aimed at?
- Future Steps
- Conclusions
- About CYS4 Srl
- About SecureFlag
Introduction
Throughout the long experience in several Red Team, Incident Response and traditional security training activities, CYS4 experienced a recurring problem: SOC structures often show limited capabilities to identify attacks and stay updated to face the latest APT (Advanced Persistent Threat), which are more and more frequent. This led to the idea of developing a new product capable of delivering a new, advanced and practice-oriented training, aimed to continuously improve the skills of SOC analysts, joint by a benchmarking and evaluation program to detect problems in the deployed technologies (e.g: SIEM).
As a matter of fact, it is essential for every SOC analyst to be able to investigate potential compromises within the organization as quickly as possible, in accordance to known «standards» as the MITRE ATT&CK framework.
With the integration of a new cloud product, entirely developed in-house, CYS4 aims to provide specialized, continuous and hands-on training for the operational components of a SOC (Security Operation Center).
Teams need to be supported with Real-World and «Hands-on Training» in order to effectively identify, recognize and fully understand alerts coming from various systems like SIEM and be quick to identify attack chains.
More effort is required to fill the gaps of the current security market landscape: that is the goal of our «Cyber-Gym», a cloud-based, virtual gym that allows a targeted and tailor-made growth path for each user involved.
A major change in the current solutions is therefore required.
Why is it made?
The utmost absence of training based on real-case scenarios has led to the realization of this project. Most of the existing courses are hugely on dependent on theoretical documentation, stretching the gap with real-world cases of a cyber attacks. Through this product, it will be possible to learn both theoretical and practical notions. The analyst will first study the main components present in enterprise environments, then moving towards realistic attacks scenarios inside computer networks to recognize how cybercriminals exploit such elements. Finally, the analyst will learn how to apply the appropriate mitigation measures.
Next, we present a few take on why it is necessary to overtake traditional learning and e-learning methods:
Classroom Training
- ❌ Expensive both on time and cost perspectives: companies must pay on-site trainers to prepare their SOC teams. This could take up a lot of training hours, possibly forcing exhausting schedules.
- ❌ Training schedule should be adjusted in order to keep activities up and running.
- ❌ On several training courses, students are assumed to be starting on the same knowledge level: this is not always the case.
- ❌ Often a one-time event that fills the user with a lot of information in a short amount of time: a typical training session take up also 4 hours per session. With this short time, a trainer must include as much information as possible. This could create confusions to the analysts.
- ❌ In most of the cases they are not technology agnostic and they do not focus on explain how an attack works and what are the best ways to detect it.
Video lectures
- ❌ Few practical examples: video lessons are often limited to a small set of cases. This prevents the analyst to try out new things during the learning process.
- ❌ Difficulty to assess obtained knowledge: video lessons don’t permit to evaluate the correct learning path of the analyst. This because there is not a direct link between the trainer and the analyst.
- ❌ Multiple choice questions: after videos or more training material, most of the platforms offer a simple form that contains questions about the presented contents. The answers, in most cases, are given in the form of multiple choices: this approach does not evaluate precisely what the analyst has really understood.
How we solve this problem?
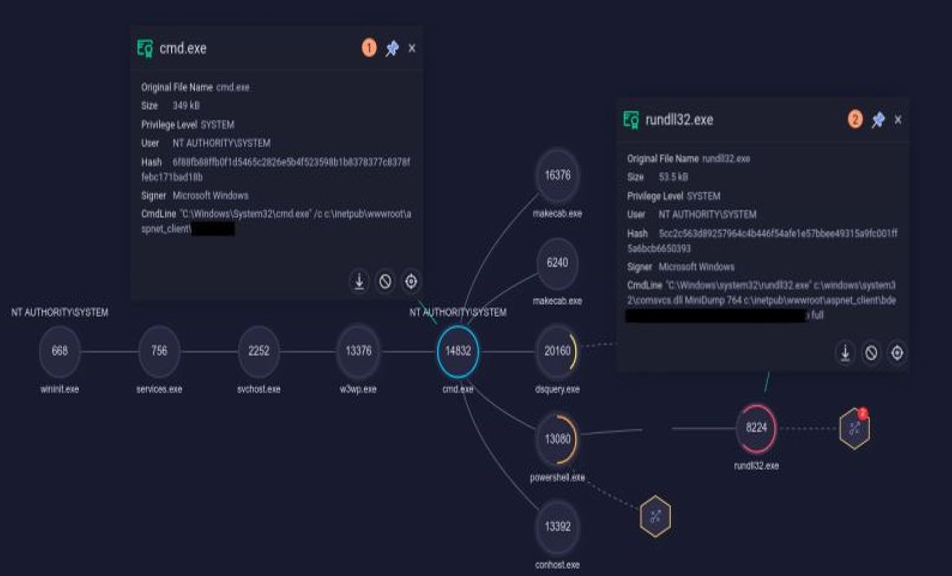
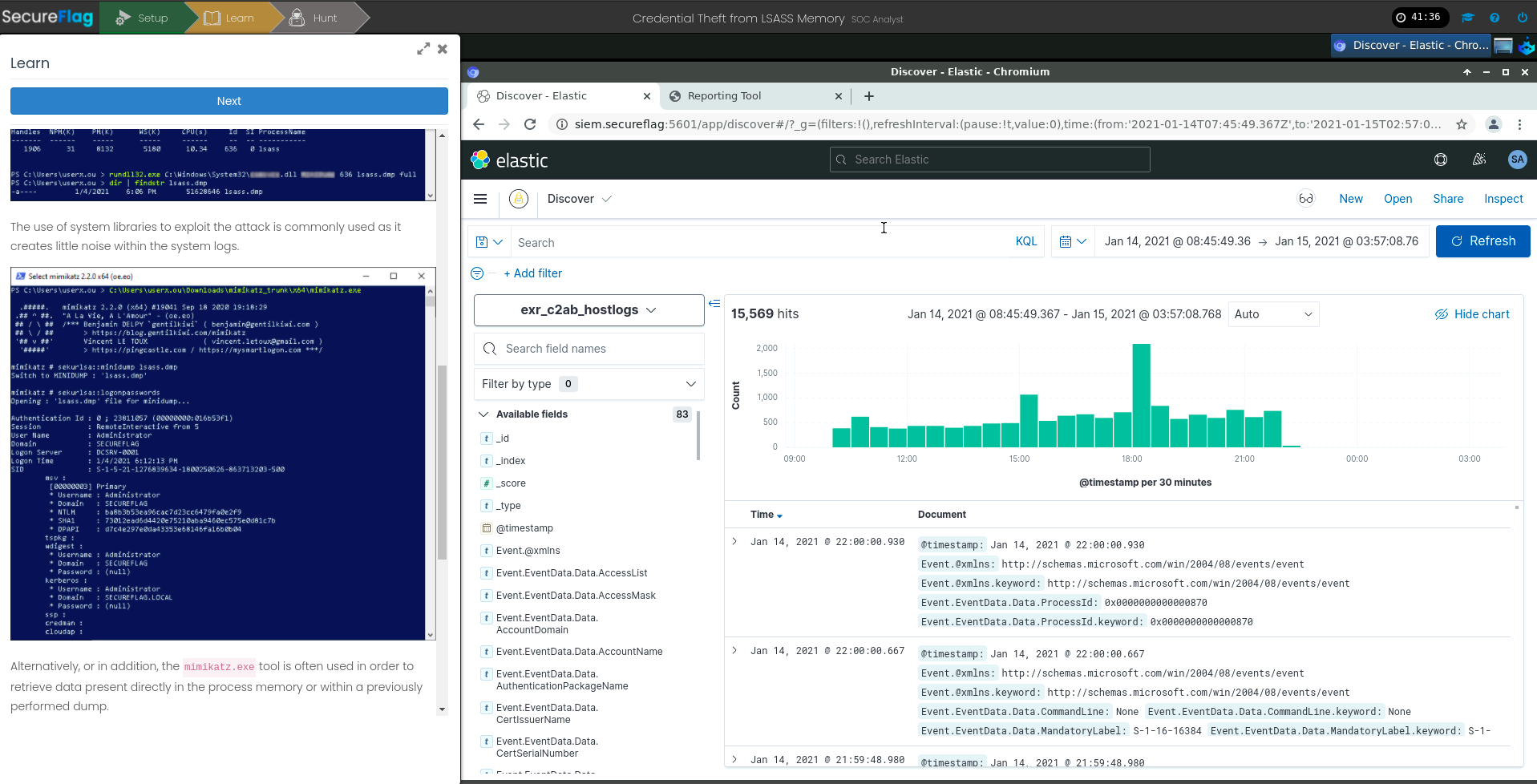
A collection of theoretical and practical contents about Incident Response methodologies and real-case scenarios, realized in collaboration with SecureFlag. The analyst will explore a training path to understand and recognize the principal attack methodologies used by the most common Advanced Persistent Threats (APT). All the exercises take place in a custom laboratory set up by the CYS4 team. It recreates realistic infrastructures based on Active Directory environments and POSIX systems. Information as logs are extracted from this laboratory, enriched by adding information from firewalls and other network devices. In this way, the analyst can trace and recognize the simulated attack methodologies throughout the whole network.
With this CTFs-like approach (Capture The Flag), we aim to replace the ineffective security trainings with hands-on labs, while lowering the costs of trainings and preparing a team with top notch capabilities in a short amount of time.
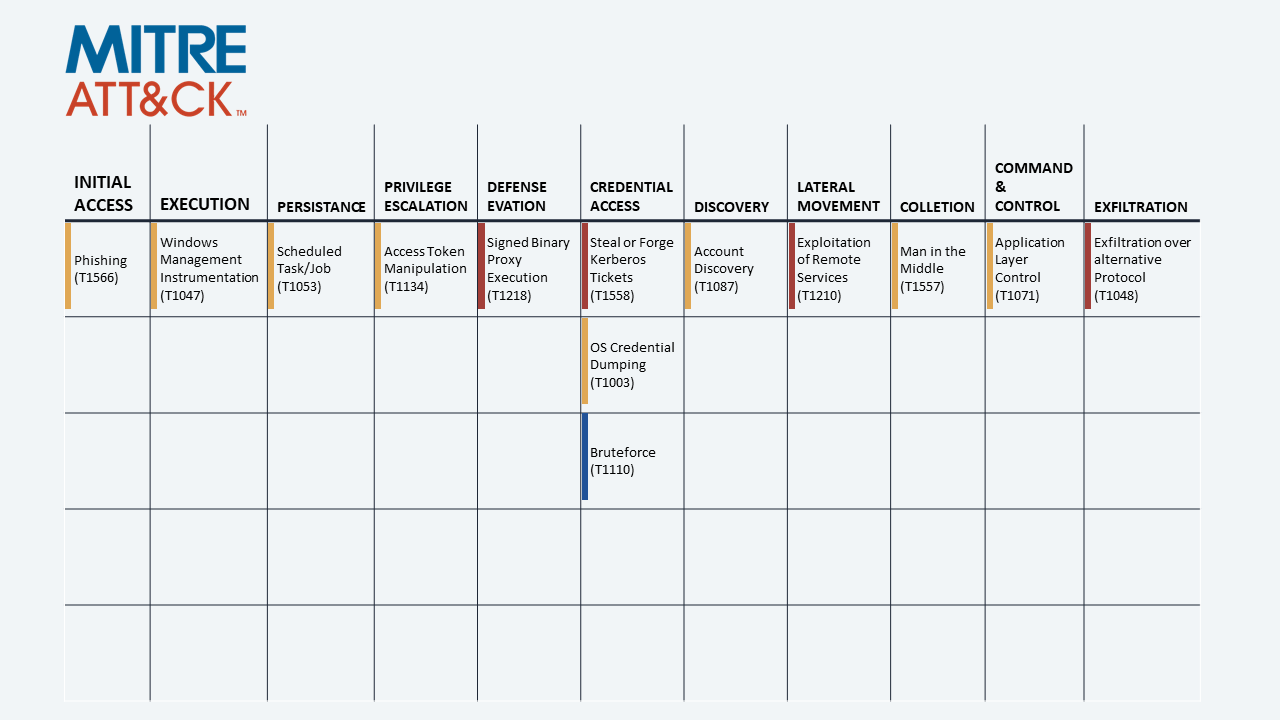
Our product offers the opportunity to walk the student through a so-called Learning Path, as a tool designed to make clear and steady learning steps. In detail, it allows the user to tackle new topics through a guided chart, in this case the kill chain of the MITRE ATT&CK framework. This approach gives a logical structure to the main phases of a typical APT.

Our course offers a large landscape of exercises and scenarios, which increase day-by-day with the latest attacks starting from real world cases.
Advanced Practical SOC Training Platform
- ✅ Helps the analyst along the way to identify, exploit, understand, and resolve security issues.
- ✅ Dedicated environment accessible in seconds, via a web browser.
- ✅ Learning makes use of the same tools used in the workplace.
- ✅ Continuous and constantly updated training.
- ✅ Large space for the theory section that makes the platform self-consistent.
- ✅ «Tailor-Made» growth paths.
- ✅ Documentation, KB and suggestions always available.
- ✅ Cost-effective.
- ✅ Hybrid learning with support as needed from CYS4 specialists.
- ✅ Real-time results and suggestions.
- ✅ Automatic scoring.
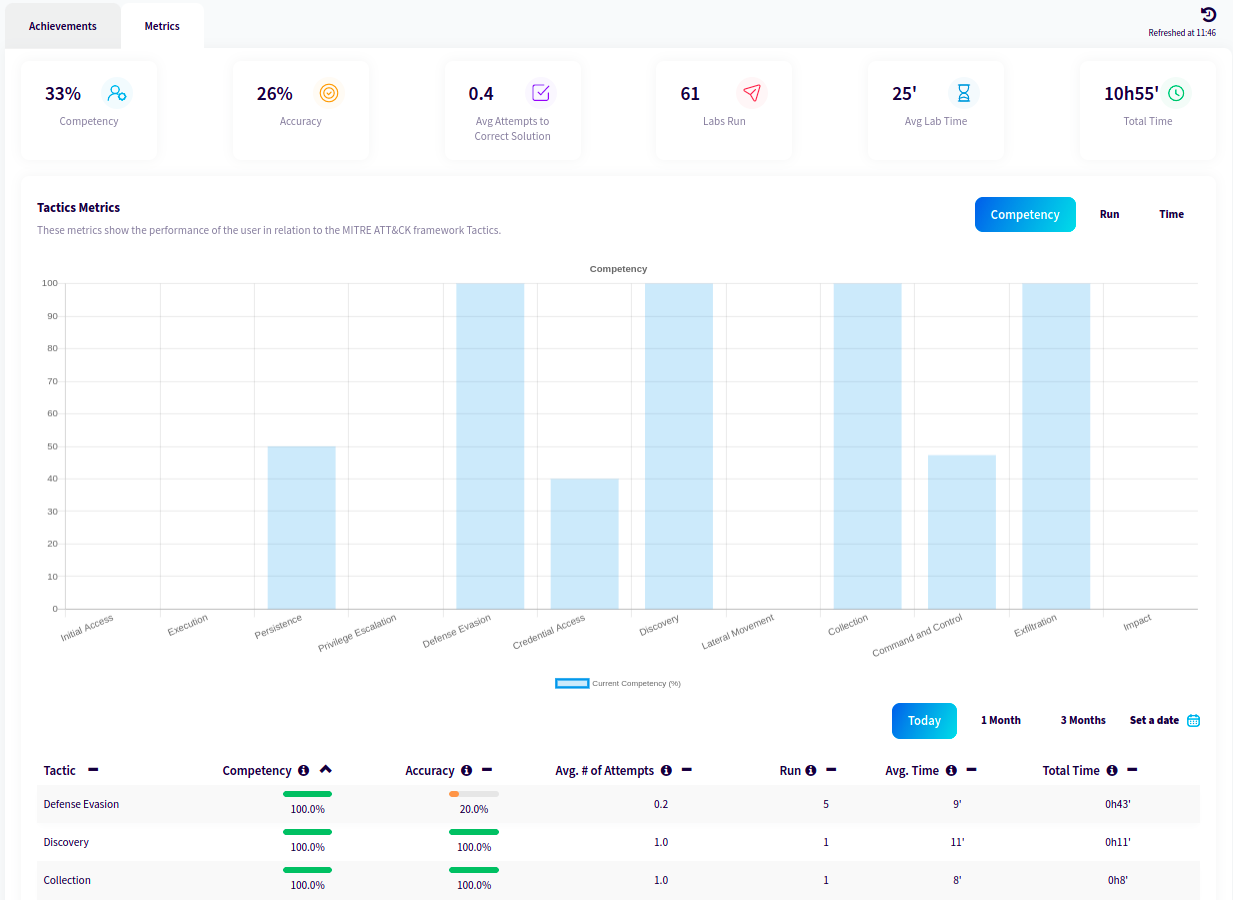
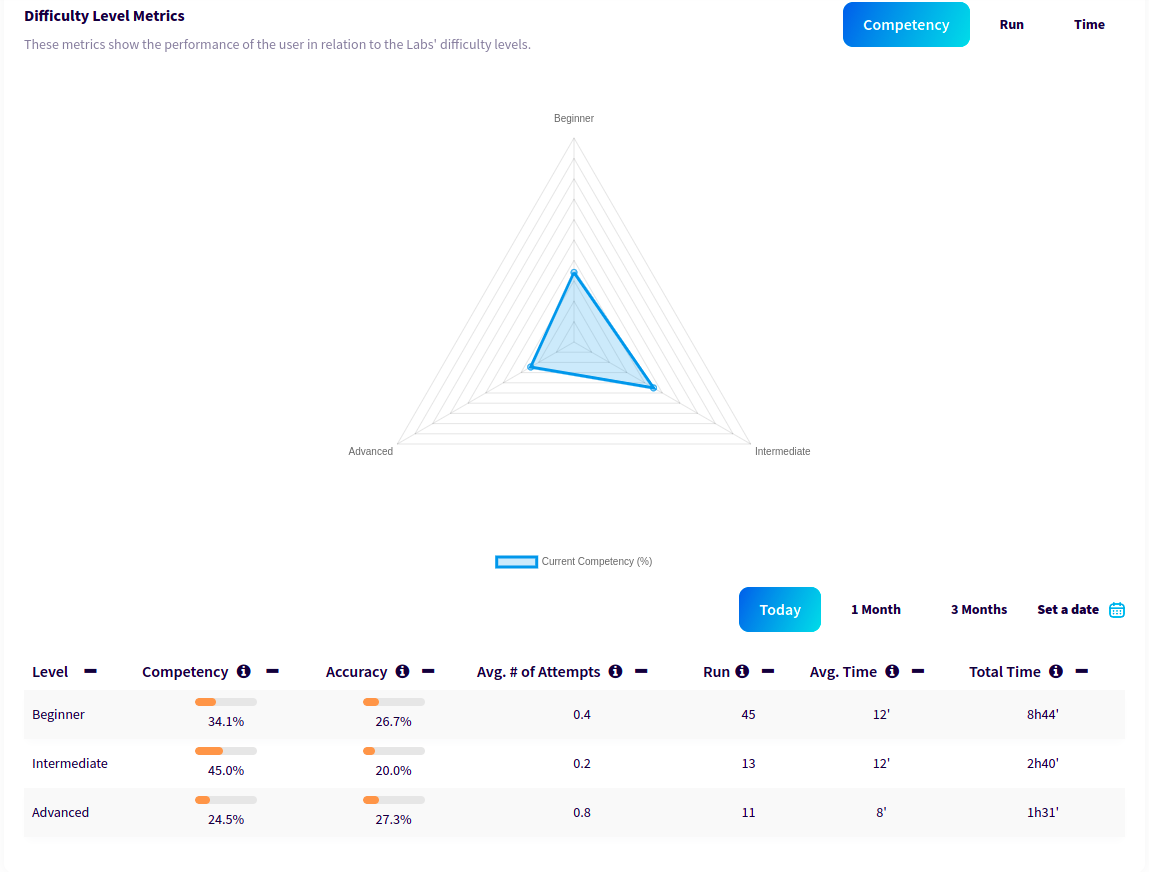
- ✅ Points, Trophies, Certifications.
- ✅ Compare results to identify personal and team growth.
- ✅ Gamification approach:
- ✅ Ability to organize time-based challenges to increase collaboration leveraging team-building.
- ✅ Participants use an active approach to solve safety problems.
- ✅ An ideal tool to engage the entire community.
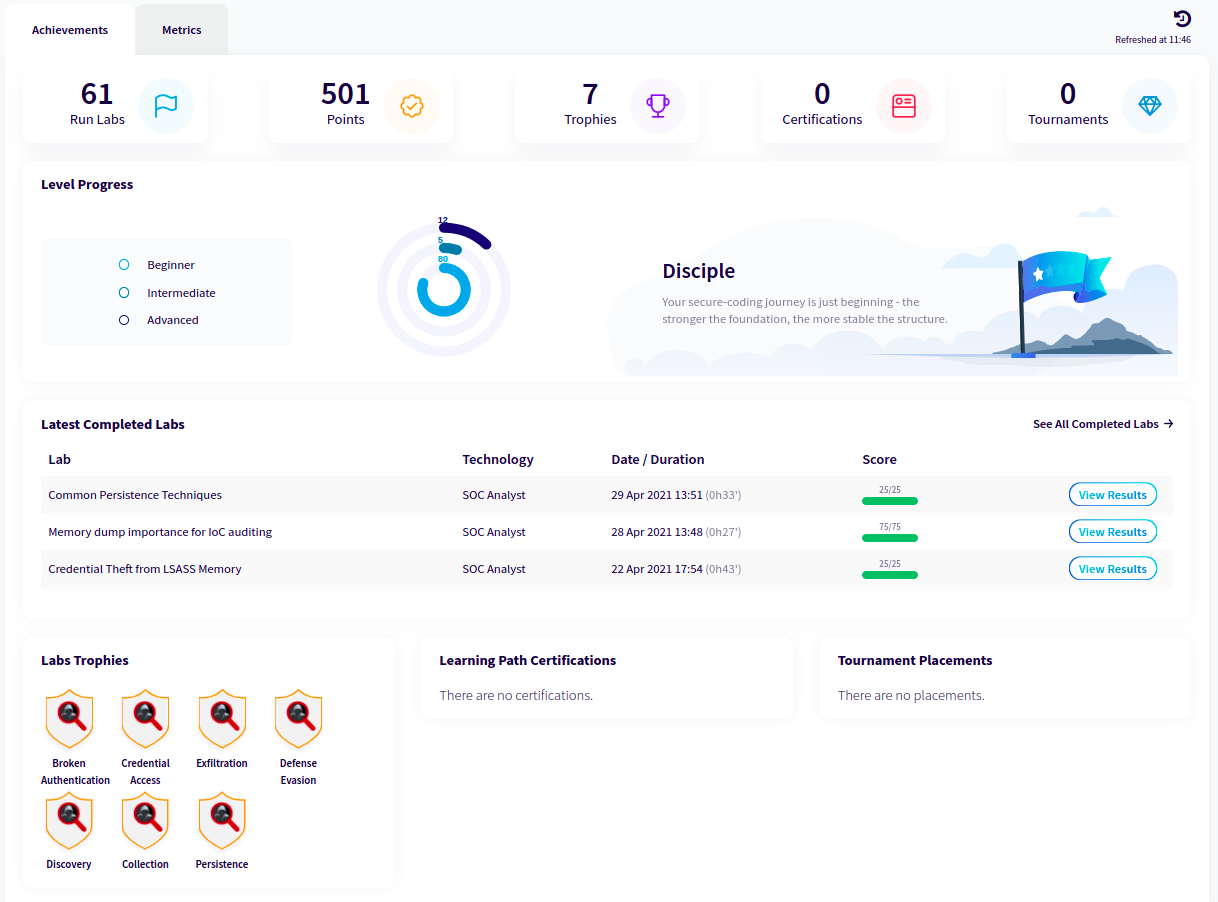
Who is it aimed at?
The project is aimed at these main professional categories:
- SOC personnel: they should be always updated to the latest threats and scenarios.
- IT personnel, primarily interested in the Issues Mitigation section.
Future Steps
- Regularly updating Tactics from real-world scenarios.
Conclusions
Our course definitely represents the best way to increase Knowledge and Threat Hunting capabilities of your SoC team. Moreover, since it is a service oriented towards Gamification, it offers a challenging environment aimed at achieving a very steep and vertical learning curve.
For any clarification, feedback or information, please send an email to [email protected].
About CYS4 Srl
CYS4 was born in 2015 from a collaboration with an Israeli company in the world of Cyber Security, then detaching its team ensuring the focus on innovation and quality towards a national context. The CYS4 team is made up of operational figures, young people and IT security experts who have chosen to make their passion a job. There are numerous vulnerability discoveries and publications by the CYS4 team on security on important products including Safari, VMWare, Skype, Outlook and IBM. CYS4 employs are highly qualified and referenced personnel, in possession of professional certifications recognized internationally. These certifications guarantee technical competence and a high ethical profile.
About SecureFlag
Special thanks to the team at SecureFlag, a security company founded in London in 2019. SecureFlag is an online training platform for Developers and DevOps engineers to learn secure coding practices. SecureFlag offers organisations an intuitive, scalable and innovative way to strengthen the skills of their development teams through a new hands-on approach based on real-world scenarios that allows to effortlessly implement iterative and individualised training to fill competence gaps. SecureFlag iprovides training to all OWASP members globally.